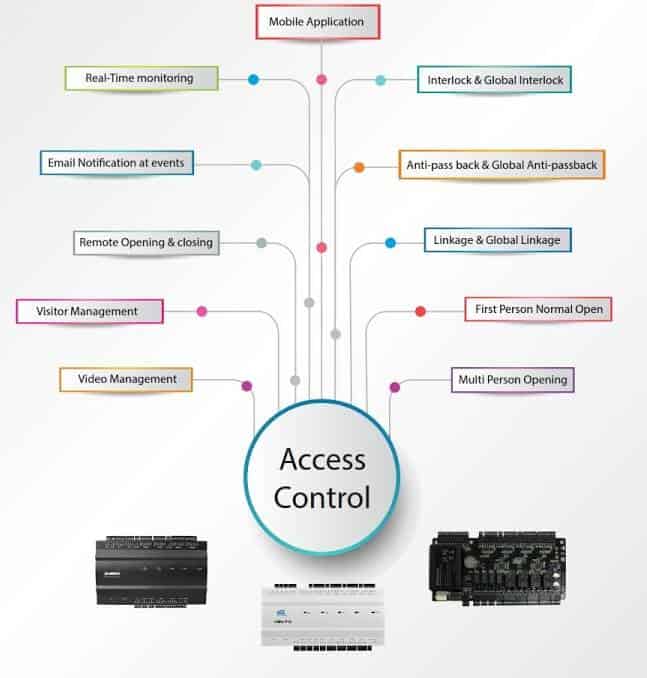
Ampletrails provides a flexible and customizable Access Control System that can work on-premise or on-cloud, depending on your choice. It can suit the access control needs of any organization, no matter its size, location, layout, or working hours. It has features such as Anti-Passback, 2-Person rule, First-In User, Blocked Users, Door Auto Re-lock, Guard Tour, Man-Trap, and Smart Card-based Identification, which make sure that your physical assets and personnel are safe and secure. The system offers simple and effective biometric security, which helps you comply with regulations, manage in-and-out operations, evaluate access levels, and count people accurately during emergencies.
Ampletrails’ complete access control solution combines user-friendly software and sturdy hardware, which guarantee perfect authentication and authorization. The web-based access control software is easy to use, allowing you to operate it independently. Experience high-quality security with Ampletrails’ integrated hardware and software, which offer strong security, user-friendly operation, and adaptability to your specific organizational needs. Trust Ampletrails for unmatched security and smooth operations in a secure environment.
User, Zone, and Time-based Access Control
Corporate environments face serious security risks from unauthorized access attempts. To prevent this, many organizations use Access Control, the popular solution for blocking unwanted entry. Access Zones, defined physical areas with specific access rules, are very important for this.
With Ampletrails Access Control Solution, organizations can control user access accurately, deciding who can enter which Access Zones and when. This strong feature helps to apply strict departmental limits, making sure that employees from one department cannot enter forbidden areas. Also, time-based access rules can be given to each zone, increasing security and flexibility.
Ampletrails gives the high-quality security needed to improve access control and protect the organizational environment from unauthorized access attempts at any time.
Access Control System Access control devices Biometric Access Control
Face Biometric Attendance Machine
Why ACCESS CONTROL SYSTEM.
An Access Control System is a security system that controls access to a physical space or resource. Access control devices, such as card readers, keypads, and biometric scanners, are used to grant or deny access to authorized individuals. Biometric Access Control is a type of access control that uses biological characteristics, such as fingerprints, facial recognition, or iris scans, to verify a person’s identity before granting access. Biometric access control systems are considered to be more secure than traditional access control systems that rely on cards or passwords.
Enterprise Access Control | Unified Control, Multi Cities
Trusted by Top Companies, Awarded In-house R&D, Pan India Service Network. Trusted by Top Indian Business. Years of Experience. 3000+ Customers.
16+ Industry Verticals. Services: Access Control, Time Attendance, Canteen Management, Visitor Management, Vehicle Access, IP CCTV.
1) Restrict Access to specific areas.
2) No need to carry multiple keys. Your RFID card, Fingerprint, Face, Password. It can be key to multiple locks.
3) Protect your valuables from authorized access.
4) Restrict the public from entering an office or area. HR Rooms, Accounts Finance.
5) Harder to duplicate as compared with Key which can be duplicated.
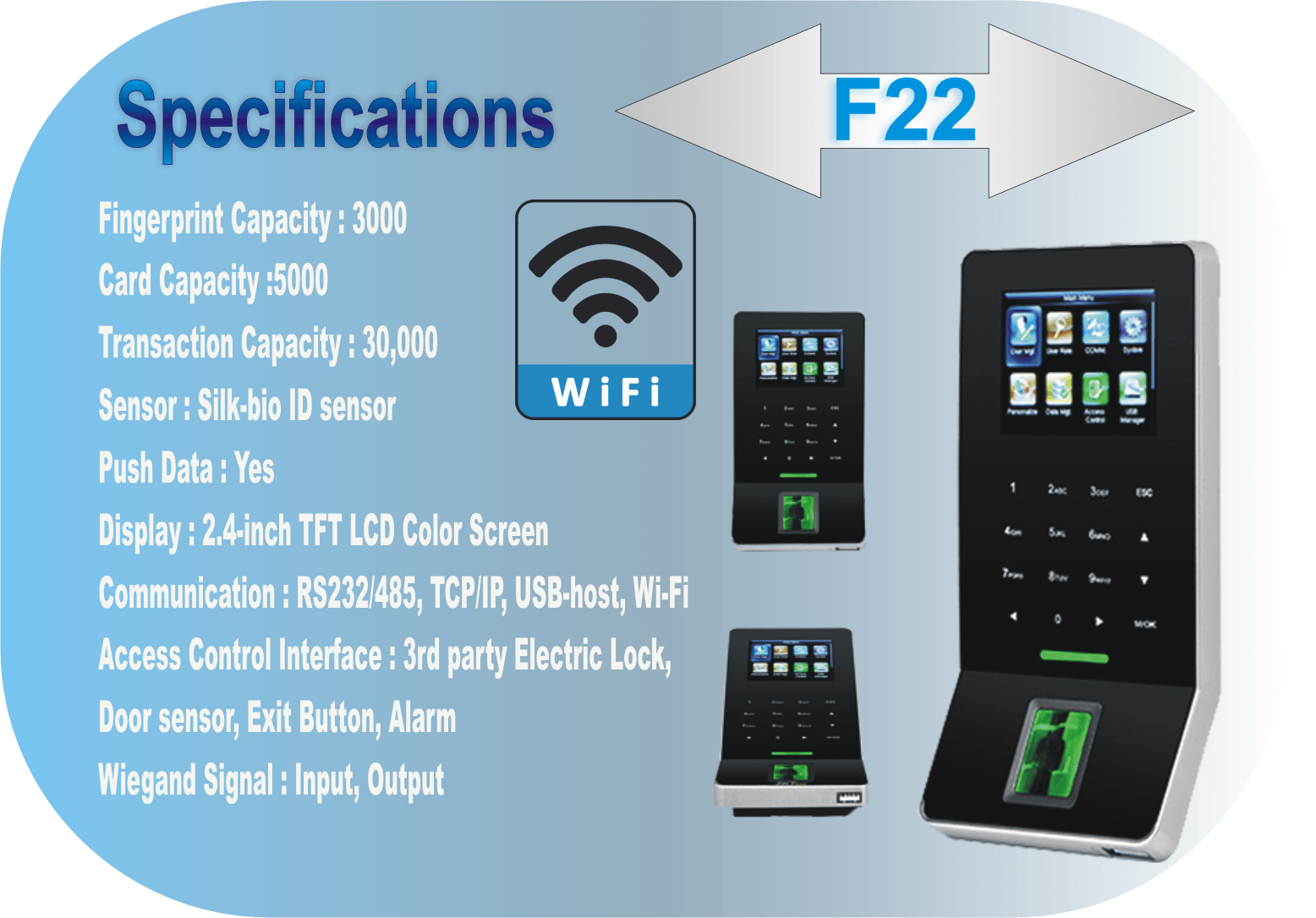
A WiFi Access Control System is a type of access control system that uses WiFi technology to grant or deny access to a network or physical space. The eSSL F22 is a specific model of WiFi access control system made by the company eSSL Security. The eSSL F22 is a standalone wireless access control system that can be used to control access to a building or other physical space. It can be configured to work with various types of access control devices, such as proximity cards, biometric scanners, and keypads.
Standalone Access Control solution doesn’t require a web‐based or network architecture. It is completely independent and works on PoE. Access Control features are inbuilt in the software itself and the user needs to configure the device, features from that mode itself. Typically, used in SOHO and SME where there is single location and requires built-in Access Control features.
6) Disable access after an employee leaves an organization.
Access Control , If you have any query or want to place an order please contact us now at 9315441078 WhatsApp 9315441053, 9034757673 or email us at in**@am*********.com of fill the below Inquiry Form.
Biometric Attendance System, Biometric Attendance Machines, Biometric Access Control System, Access Control System Suppliers, Fingerprint Attendance System, Time Attendance System in India, Standalone Biometric Attendance Machines, Biometric Attendance Recorder Supplier
[su_heading]Centralized Biometric Authentication[/su_heading]
Access Control System for Data Centers
When it comes to data centers, security is of the utmost importance. With so much valuable information stored in one place, it’s crucial to have a system in place to keep it safe and secure. One way to accomplish this is by implementing an Access Control System.
An Access Control System (ACS) is a security solution that controls access to a physical space or resource. It can be used to restrict entry to certain areas, such as server rooms, to authorized personnel only. ACS can be integrated with other security systems, such as CCTV cameras, to provide a comprehensive security solution.
One of the biggest benefits of an ACS is that it can be tailored to fit the specific needs of a data center. For example, it can be set up to only allow access to certain areas during certain times of the day. This can be especially useful for data centers that are open 24/7, as it allows for greater control over who has access to sensitive information.
There are many different types of ACS available, such as card-based systems, keypad-based systems, and biometric systems. Biometric systems, such as fingerprint or facial recognition, are considered to be the most secure. They ensure that only authorized personnel are able to access restricted areas, as they use unique biological characteristics to verify a person’s identity.
Another advantage of an ACS is that it can be integrated with other security systems, such as CCTV cameras and intrusion detection systems. This allows for a higher level of security, as it provides a more comprehensive solution. For example, if someone tries to enter a restricted area using a forged ID, the CCTV cameras will capture the incident, and the ACS will deny access.
In conclusion, an Access Control System is an essential security solution for data centers. It provides a way to control who has access to sensitive information, and it can be integrated with other security systems for added protection. Whether you’re looking to secure a small server room or an entire data center, an ACS is a smart investment.
Biometrics provides high-end security over RFID and hence integrating biometrics with Access Control solution fetches complete security for Data Centers. Usually, an employee needs to punch twice in order to access the data rack of his/her organization.
First Punch: A Biometric device will be installed at the entrance of the data center. The user will punch on the device and accordingly he will be granted/declined access. This authentication ensures that an authorized user is trying to access the data center.
Second Punch: Once the user is granted access, he or she will punch again at the device installed near the screen in order to access the respective racks. Once the user punches, the screen will display the list of racks that he or she is allowed to access. For Example – when ‘x’ employee of ‘ABC Organization’ makes his second punch, the screen will display the list of only ABC Organization racks that are allotted to him. The user then needs to select the racks that he wants to access from the screen and accordingly, he will be granted access.
Pre-defined Rack Access:
Every company has designated racks allotted to them. Admin can define the racks company wise, which means whenever a user makes his second punch – only racks allotted to his respective company will be listed on the display screen.
This feature acts as USP for data centers as they can ensure that a rack of company “x” will not be accessible to or misused by an employee of company “y”
Rack accessible for a defined time period:
Every rack that is allocated to a company can only be accessed for a definite period of time. Admin can set the duration and accordingly the rack will be accessible for the pre-defined time period.
Our Operation Area:
Gujarat, Chandigarh, Delhi, Hyderabad, Surat, Jaipur, Lucknow, Nagpur, Patna, Indore, Bhopal, Ludhiana, Agra, Raipur, Uttar Pradesh, Allahabad, Kolkata, Tamil Nadu, Chennai, Rajasthan, Jalandhar, Ropar, Mohali, Punjab, Mumbai, Nashik, Pune, Maharashtra, Madhya Pradesh, Jabalpur, Kerala, Bangalore, Karnataka, Hubli, Himachal Pradesh, Shimla, Vadodara, Ajmer, Kanpur, Varanasi, Visakhapatnam, Ghaziabad, Faridabad, Rajkot, Amritsar, Ranchi, Coimbatore, Kota, Guwahati, Gurgaon, Noida, Jhansi, Jammu, Udaipur, Patiala, Mathura, Hisar, Sonipat, Panipat, Alwar, Jodhpur, Srinagar, Pinjore, Warangal, Baddi, Nashik, Trivandrum, Ludhiana, Vijaywada, Ahmedabad, Kochi, Nellore, Mysore, Bihar, Chhattisgarh, Nagpur, Kanpur, Jaipur, Kurukshetra, Sonipat, Andhra Pradesh, West Bengal, Goa, Surat, Ambala, Saharanpur


 Matrix Cameras
Matrix Cameras Matrix Product
Matrix Product Biometric Machines
Biometric Machines